How to Use Proxy Server? Definition, Classification, and Usage Guide

When it comes to network security, privacy protection, and access control, proxies are a common technical concept. They provide users with an effective way to forward network requests through an intermediary server, hiding the real IP address. This technology has broad applications in today's digital society, not only for protecting personal privacy but also for offering a safer network environment for businesses and institutions.
What is a Proxy Server?
A proxy is a network technology that communicates through an intermediary server, acting as a forwarder to send user requests to the target server. During this process, the proxy hides the user's real IP address, only displaying the proxy server's IP address to the target server. This technology can be used to protect user privacy, bypass geographical restrictions, enhance security, and support specific network activities, but must be used in compliance with relevant regulations and terms of service.
Proxies can be widely applied in data collection, access control, content filtering, and network performance optimization. By using proxies, users can change their online identity, control access, and manage their online presence. This technology is important for businesses monitoring employee internet activities, protecting personal privacy, and enhancing network security.
Two Forms of Proxies
| IP | Port | Username | Password | |
| IPv4 | 127.0.0.1 | 8080 | username |
password |
| IPv6 |
2001:0db8:85a3:0000:0000:8a2e:0370:7334 |
80 | username |
password |
First, proxies are crucial for personal privacy protection. On the internet, personal privacy information may be monitored, tracked, or collected. Using proxies can prevent websites or malicious users from tracking your real IP address, protecting personal identity and location information.
Second, bypassing geographical restrictions is another common use of proxies. Some websites or services restrict access based on IP addresses, preventing users from certain regions from accessing them. By using proxies, users can appear as if they are from other regions, bypassing these geographical restrictions to access restricted content or services.
Additionally, proxies can improve network security. Businesses can set up proxy servers to monitor and filter network traffic, identifying and blocking potential malicious traffic and attacks. Proxies can also optimize network performance by caching frequently used resources or accelerating data transmission, enhancing the user experience.
However, the use of proxies also carries some risks and legal limitations. Some regions or service providers may restrict or regulate proxies because they can be used for illegal activities such as network attacks, data theft, or violating terms of service. Therefore, when using proxies, it is essential to comply with local laws and service provider regulations to ensure legal and compliant usage.
Proxies are a powerful network technology that provides users with ways to protect privacy, bypass geographical restrictions, and enhance network security. However, they must be used cautiously, following legal regulations to ensure their legitimate and compliant application.
What are the Types of Proxies?
Proxies can be categorized in different ways. Here are some common classifications:
By Level of Anonymity:
Transparent Proxies: Forward requests while revealing the real IP address, allowing the target server to obtain the user's real IP information.
Anonymous Proxies: Hide the user's real IP address, but the target server knows you are using a proxy and cannot directly obtain your IP address.
Elite Proxies: The most secretive type, hiding both the real IP address and the fact that a proxy is being used, making it undetectable by the target server.
By Protocol:
HTTP Proxies: Can only handle HTTP requests, suitable for web browsing and basic online operations.
HTTPS Proxies: Can handle HTTPS requests, offering a higher level of security for encrypted website access.
SOCKS Proxies: Support TCP connections and UDP traffic forwarding, providing broader support for various network applications.
By Server Location:
Public Proxies: Publicly available proxies that anyone can use. They may be slower and less stable.
Private Proxies: Proxies obtained through payment or personally owned, offering faster speed and more stable connections, suitable for specific individuals or businesses.
By Stability:
Static Proxies: Fixed proxies that allow users to use the same IP address for a long period.
Rotating Proxies: Proxies that change periodically, allowing users to use different IP addresses over time to avoid blocks or tracking.
These classification methods help users choose the most suitable type of proxy based on their needs, considering factors like privacy, security, stability, and access purposes.
How to Use Proxies on an Android Phone?
Materials:
Android Phone: Ensure the phone is connected to a network.
v2rayNG App: Download and install the v2rayNG app from the app store. (Installation Package) Version V 1.7.30 is recommended.
Valid SOCKS5 Proxy Address and Port: Obtain a valid proxy address and corresponding port information.
Download and Install v2ray
Download v2ray from the Google Play Store or the v2ray official site. The official v2ray repository is on GitHub, but with many versions available, I personally prefer the v2rayNG version!

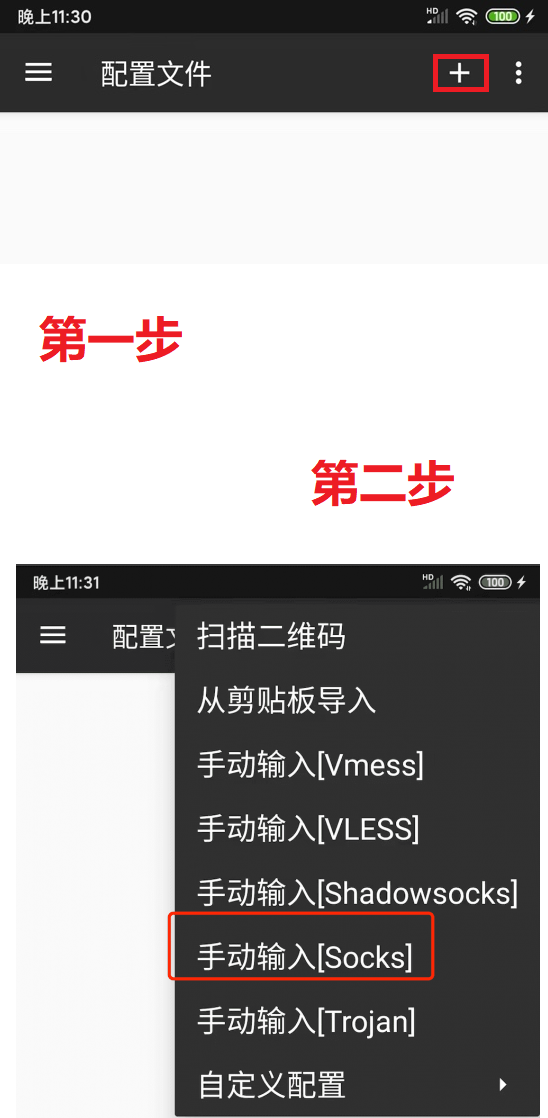
Open the v2ray app, click the + sign on the sidebar, and select "Manual Input [Socks]". Ensure the account information is complete and accurate, with no spaces or errors in the username or password!
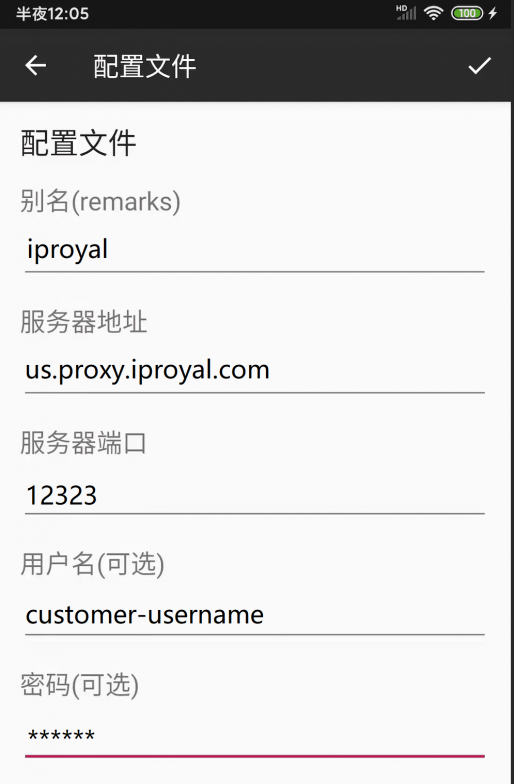
Enter SOCKS5 Proxy Information Correctly
Following the previous step, correctly fill in the SOCKS5 proxy information you purchased.
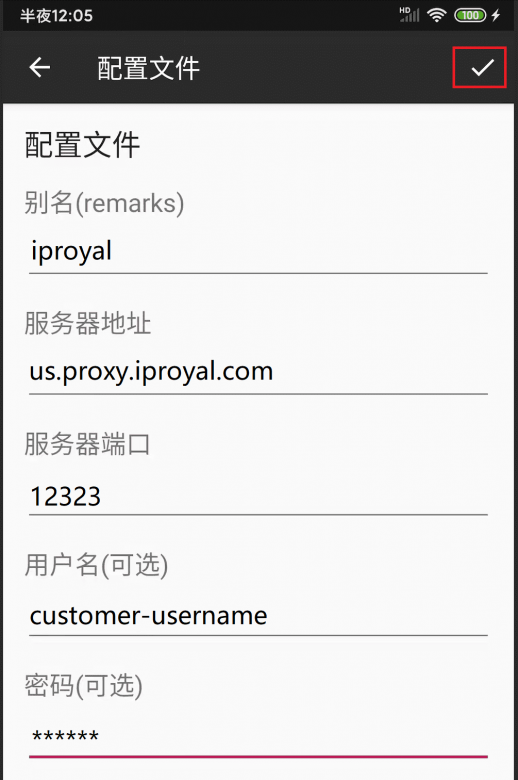
Save Information
After confirming the information is correct, click the ✓ in the upper right corner to save the node information.
Set Proxy
The interface will return to the proxy node list. Open the menu in the upper left corner and click Settings:
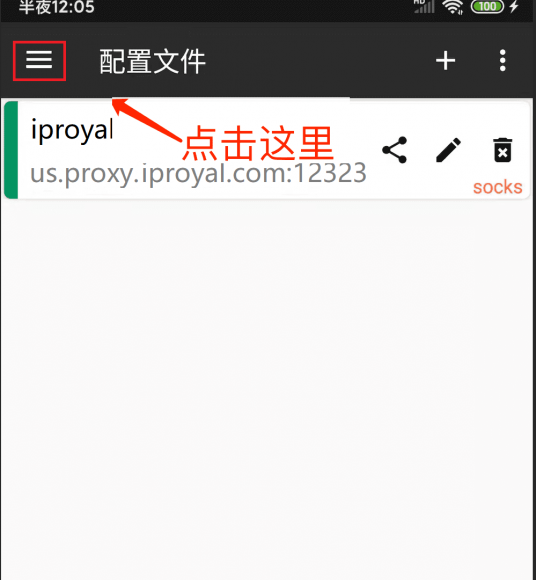
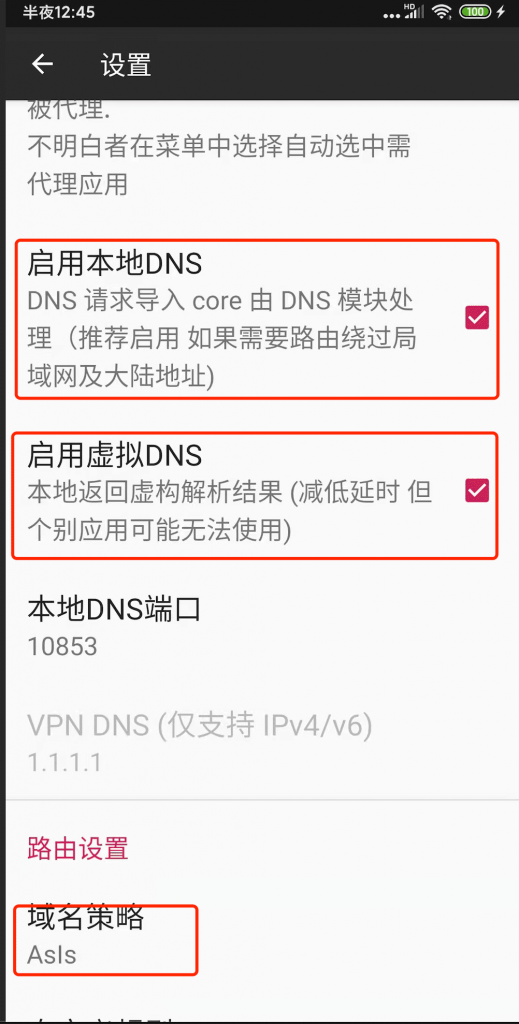
Set DNS and Local Routing
Select Enable Local DNS, Enable Virtual DNS (ignore if this option is unavailable), and choose Asls for the domain strategy (recommended), then return to the list page:
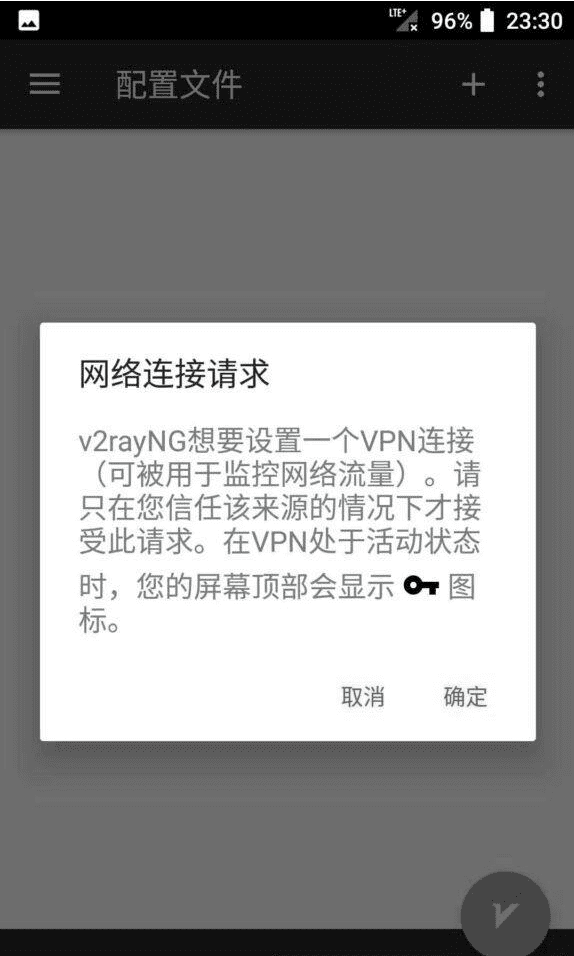
Start v2ray Proxy
Select (click) the node we just added, then click the button in the lower right corner of the screen to connect to our node:

Check Proxy
If a ? symbol appears in the phone signal bar, it means your proxy has been successfully activated. You can also click at the bottom of the software to check the proxy's ping value.
How to Use Proxies on a Windows PC?
Configuring the v2rayN software on a Windows PC to achieve global SOCKS5 proxy is an effective method to route all network traffic through the v2rayN proxy server, achieving a more secure and private network connection. Here are the general steps:
Download and Install v2rayN
Download and install v2rayN software: Visit the v2rayN official website or GitHub page to download the latest version of the v2rayN software package. Install v2rayN: Run the installer and follow the instructions to complete the installation process. Once installed, launch the v2rayN software.
Installation Package: https://github.com/2dust/v2rayN/releases
Installation Guide
Software Directory
After downloading, locate an appropriate directory, preferably not on the system drive, and extract the compressed package. The extracted directory should look like the image below.
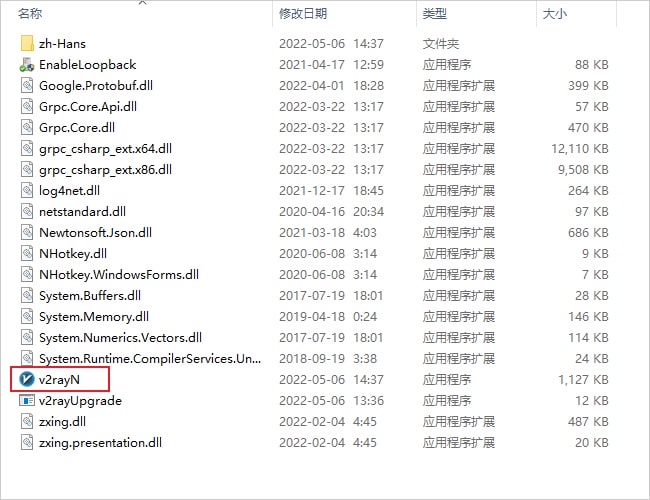
Right-click to run v2rayN.exe as an administrator. Once the program starts, it will minimize to the system tray in the lower right corner. Double-click the blue V icon in the system tray to open the main interface of the software.
Icon Explanation
The software's icon color changes according to its status. Refer to the table below for icon color descriptions.
Node
Nodes are the servers within the software. Before use, you need to add a v2rayN node to enable proxy internet access. More nodes can be found on this site's node subscription address.
Free Nodes
Since the software supports VMess, VLESS, Trojan, Socks, Shadowsocks, and other proxy protocols, you can click here to get free nodes by registering for free.
Paid Nodes
If free node resources are insufficient or unstable, consider purchasing paid nodes. We recommend V2rayA Airport, which supports Shadowsocks and V2Ray protocols and offers multiple data centers and packages to choose from.
Add Server
After obtaining node server information, you can start adding servers. Click the server button on the main interface of the software and add different node servers according to the nodes.
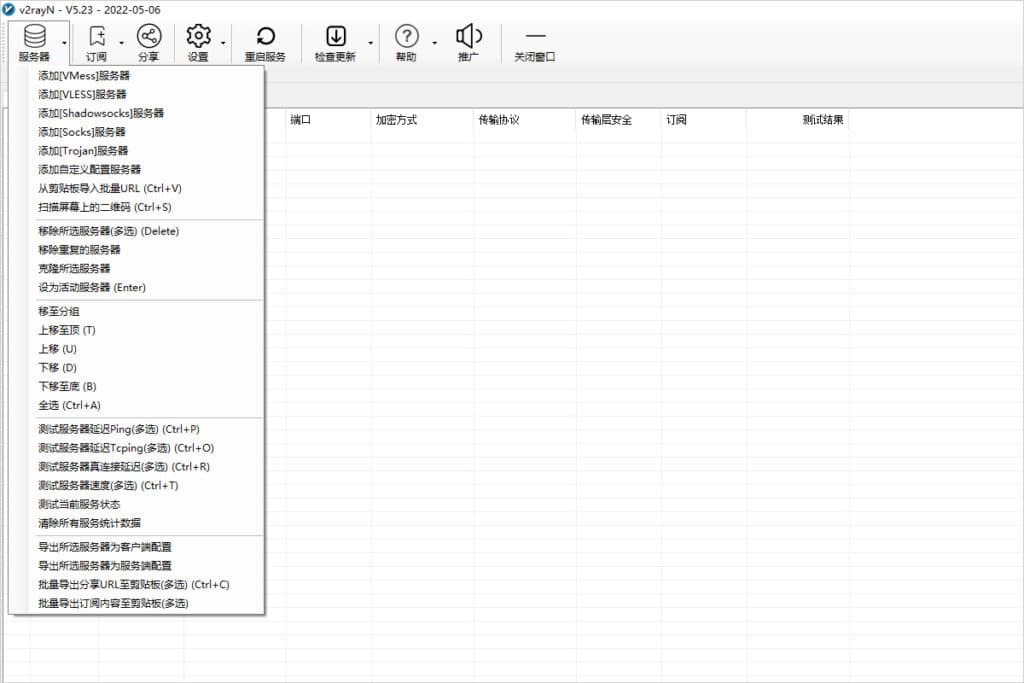 Server Settings
Server Settings
Configure SOCKS Nodes
Click the Server button on the main interface of the software, select Add [Socks] Server, as shown in the image below.
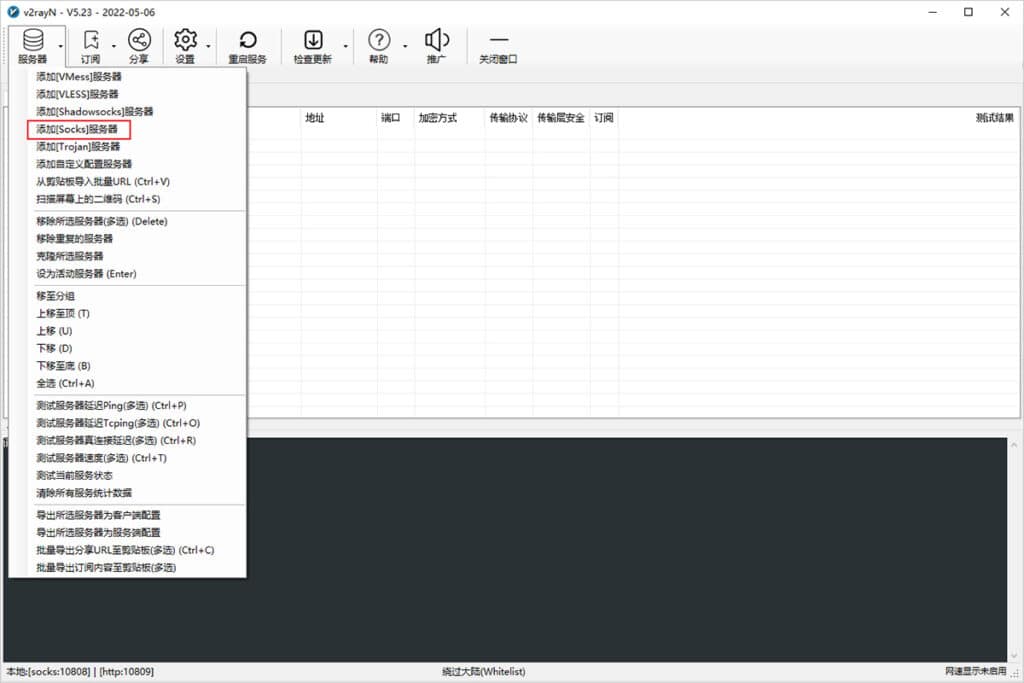 Add Socks Node
Add Socks Node
Enter the Socks node information in the add window to configure the Socks server information, then click OK to save, as shown below.
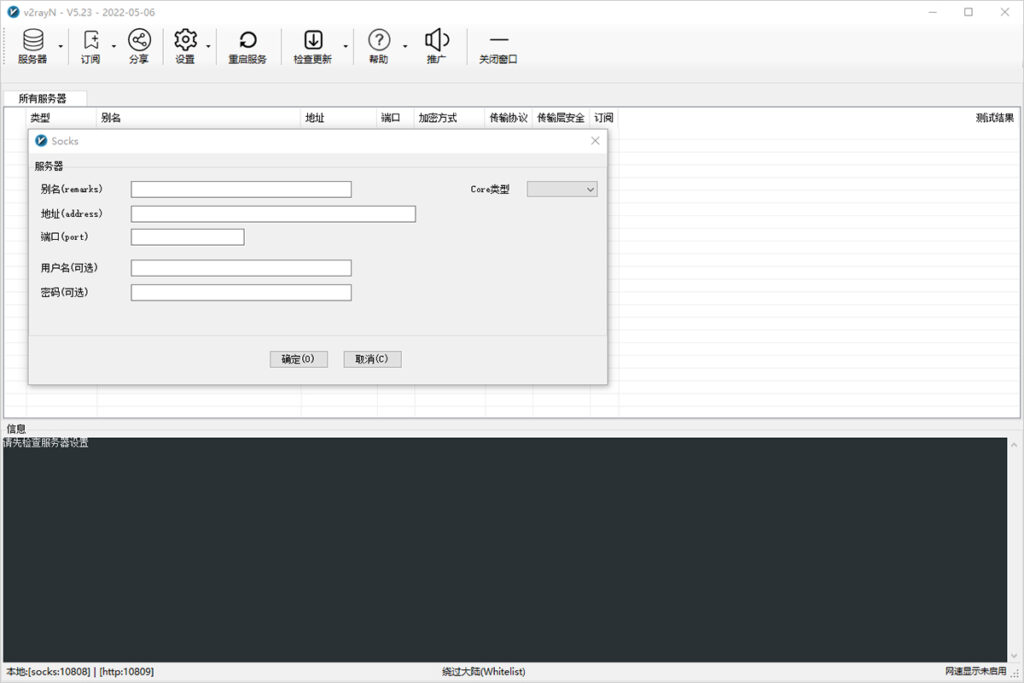 Configure Socks Node Information
Configure Socks Node Information
Usage Guide
After adding the node information, enable the system proxy and select the routing mode to start using the proxy server, as described in the System Proxy and Routing Mode sections below.
System Proxy
After configuring the server (node) as described above, set the system proxy to enable the browser to access the internet via proxy. Find the software icon in the system tray in the lower right corner, right-click it, find System Proxy, and click Auto-configure System Proxy. The software icon will turn red, indicating that you can start using it. Open Google and see if you can access it.
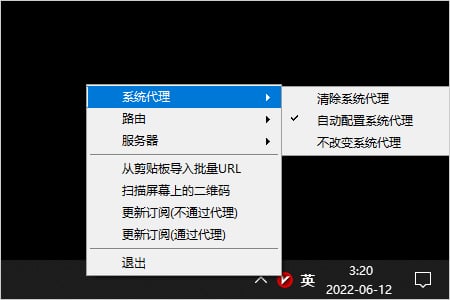 Auto-configure System Proxy
Auto-configure System Proxy
Routing Mode
Routing functionality sends inbound data through different outbound connections as needed to achieve selective proxying. A common use of this feature is to separate domestic and international traffic, sending them through different outbound proxies. There are three routing modes to choose from.
-
Whitelist Mode: Only websites in the whitelist access the internet through the node server
-
Blacklist Mode: All websites except those in the blacklist access the internet through the node server
-
Global Mode: All websites access the internet through the node server
Choose the appropriate routing mode according to your needs; generally, whitelist mode is recommended.
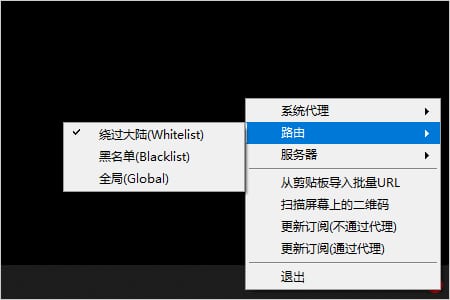 Routing Mode
Routing Mode
Auto Start at Boot
Click the Settings button on the main interface of the software, then click Parameters Settings to enter the parameters settings page. Select the v2rayN Settings tab, check the Auto Start at Boot checkbox, and click OK, as shown below.
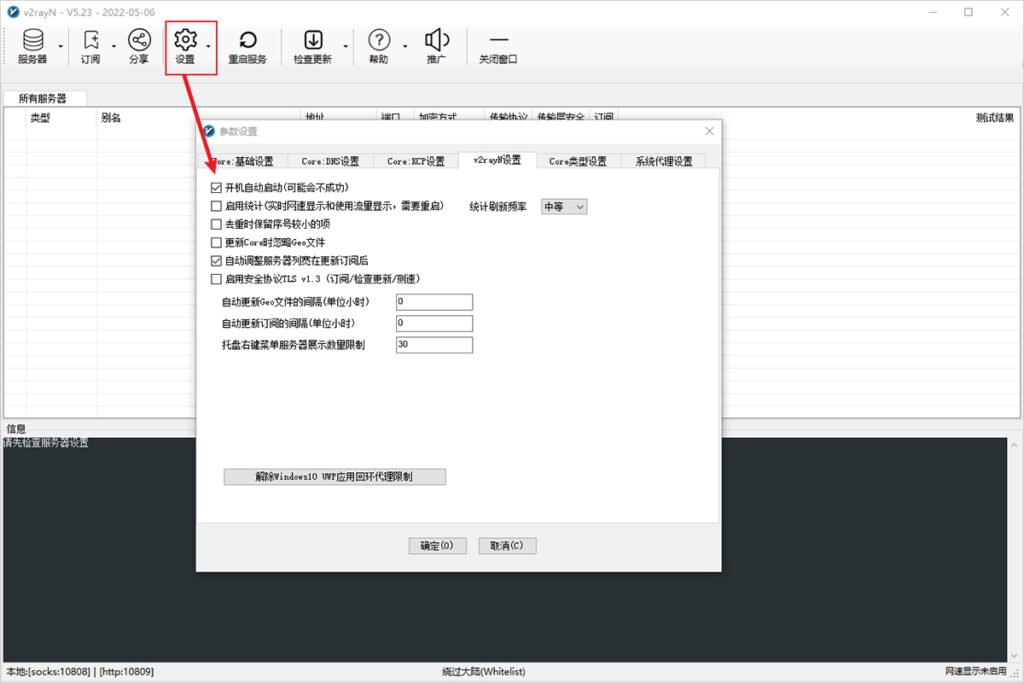 Auto Start at Boot
Auto Start at Boot
Update Guide
Online automatic updates for the software, v2fly-Core, Xray-Core, and Geo files can be done by clicking the Check for Updates button on the main interface of the software, as shown below.
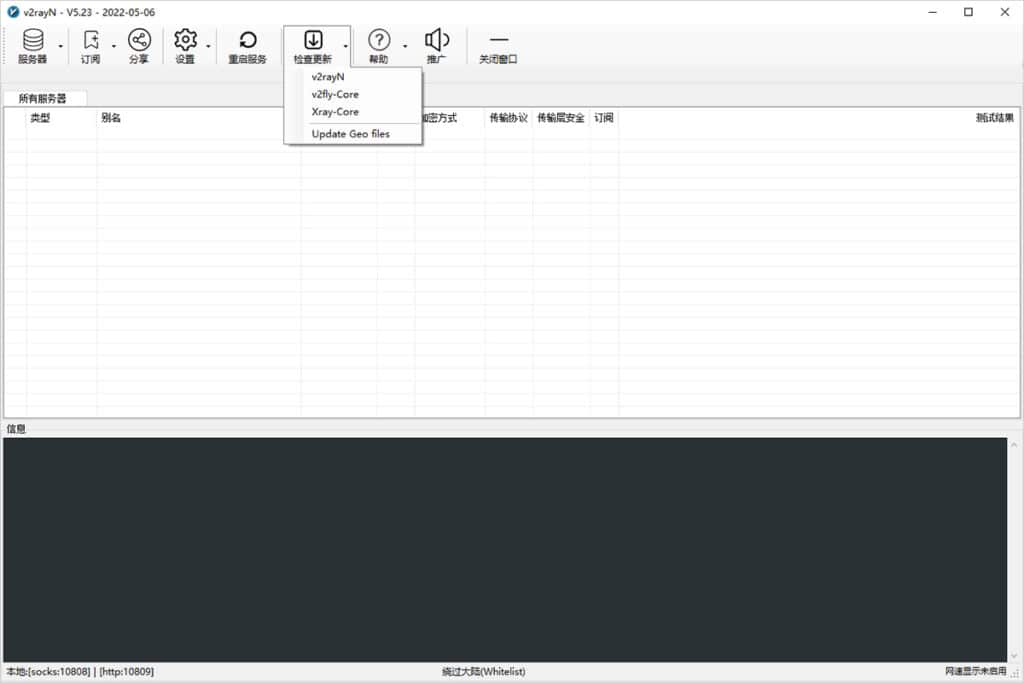 Check for Updates
Check for Updates
How to Configure Proxies in Chrome (Google Chrome)?
Install Proxy SwitchyOmega (if you have already installed it, you should know how to set up proxies with the SOCKS5 protocol, port 2333)
Online Installation: Install from Chrome Web Store
Manual Installation:
In the Chrome address bar, type chrome://extensions to open the Extensions page, then download Proxy SwitchyOmega, drag the downloaded SwitchyOmega_Chromium.crx file to the Extensions page to install it. Click Add Extension to complete the installation.
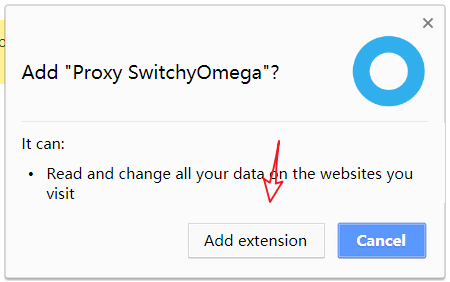
After completing the installation of Proxy SwitchyOmega, the browser will automatically open a SwitchyOmega options window. Choose Skip Tutorial.
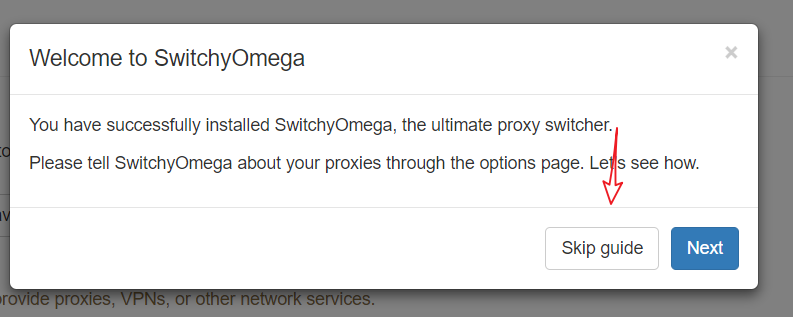
Select Import/Export, Online Restore, and input: https://github.com/FelisCatus/SwitchyOmega/wiki/GFWList.bak
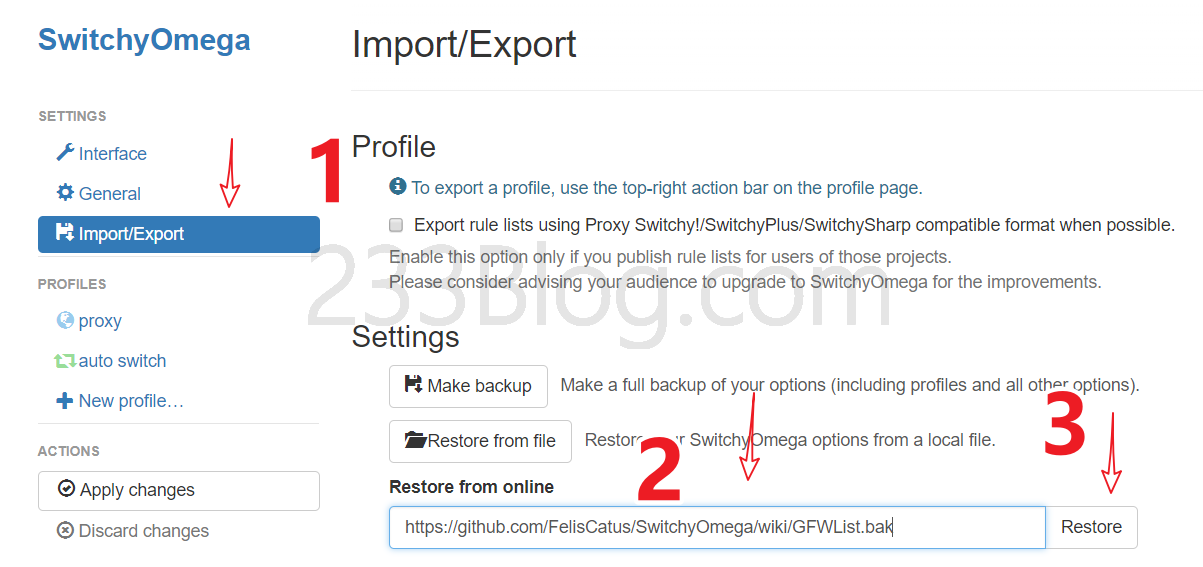
Select GFWed, set the proxy port to 2333, then click Apply Options.
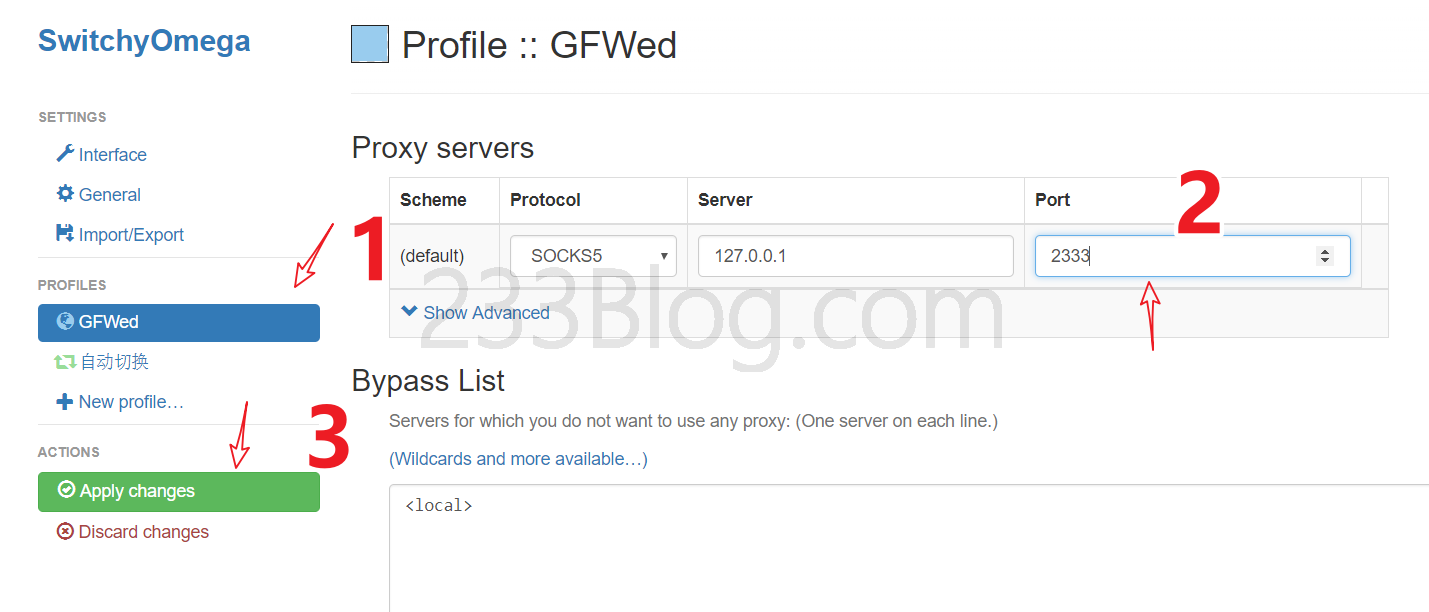
Then find the Proxy SwitchyOmega icon in the upper right corner, click it, and then click Auto Switch.
Proxies are widely used in network security, privacy protection, and access control, with applications spanning multiple fields. First, proxies can protect personal privacy by hiding the user's real IP address, preventing personal information from being tracked or disclosed. Second, they can help users bypass geographical restrictions to access restricted content or services. Additionally, proxies can enhance network security, being used in enterprise environments to monitor and filter network traffic, identifying and blocking potential malicious traffic and attacks. Understanding the applications of proxies helps leverage their functionality to enhance network security and personal privacy protection.
Configuring proxies requires several key steps to ensure the proxy service operates correctly. First, choose a reliable proxy provider and obtain the necessary proxy server information, including the address, port, and authentication details. Next, enter the relevant server information in the chosen proxy software or settings and start the proxy service. Finally, adjust the system or application proxy settings to route traffic through the proxy server. To ensure the stability and reliability of the proxies, regularly check the proxy connection to avoid network interruptions or leaks caused by connection issues.
While proxies offer many advantages and applications, their use should be carefully considered, and compliance with relevant laws and terms of service is essential. Some regions or service providers may restrict or regulate proxies due to potential misuse for illegal activities, such as network attacks, data theft, or violating terms of service. Therefore, when using proxies, it is crucial to understand and comply with local laws and regulations, and use them legally to ensure network security, personal privacy, and avoid potential legal risks.
How to Use Proxy Server? Definition, Classification, and Usage Guide Review FAQ
As a secure and fast instant m...
Pinterest has become an essent...
Gmail has become a crucial com...
Static residential proxies and...